Technology has affected all kinds of industries all over the world. This technology, which is involved in business processes in routine life, provides serious convenience in business life. Speeding up production and reducing the margin of error are some of the features it offers. The topic we will talk about today will be about Scada systems and security. Now, before wasting time, let’s take a look at what Scada is. So, let’s examine how we can ensure the security of these systems.
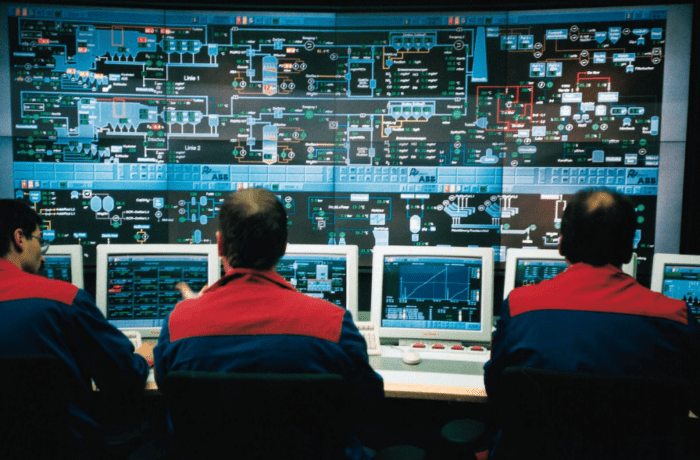
Scada; It is an abbreviation of the English phrase “Supervisory Control and Data Acquisition”. Scada is a control system architecture that uses computers, networked data communications and graphical user interfaces for high-level process control management. However, it can also use other peripheral devices such as PLC and PID controllers to interface with the process plant or machine.
Scada is a system of software and hardware elements that enables industrial organizations to:
- Ability to control industrial processes locally or in remote locations,
- Recording events to log file,
- Real-time monitoring, collection and processing of data,
- Interact directly with devices such as sensors, pumps, valves, motors and more via human-machine interface (HMI) software.
The goal of Scada systems is to help maintain efficiency, process data for more rational decisions, and communicate system problems to reduce fault processes. Therefore, it is important for industrial organizations. Scada software processes, distributes and displays data; It helps operators and other workers analyze data and make important decisions. For example, the Scada system quickly informs the operator that the failure rate of a product group is high.
The operator pauses the operation and displays SCADA System data through an HMI to determine the cause of the problem. The operator reviews the data and finds that the machine 4 is faulty. The ability of the Scada system to report a problem to the operator helps it resolve the issue and prevent further product loss.
So, in which sectors are Scada systems mainly used?
Scada systems; It is used in electricity, manufacturing, energy, wastewater, transportation, recycling, food, beverage, oil, gas and many other industrial establishments. Effective and giving importance to security, Scada systems provide serious benefits to industrial organizations in terms of time and money.
Now, after talking about some advantages and disadvantages of Scada systems, we will move on to the security aspect. Some advantages of Scada systems;
- The system provides the ability to store large amounts of data,
- Quick response,
- It is possible to obtain real data simulations with the help of operators,
- Scalable and flexible when adding additional resources,
- It can be used in many industrial establishments,
- With advanced software, data can be viewed from anywhere, not just the local site.
So what are the disadvantages of Scada systems?
- Installation costs are high,
- The system supports limited software and hardware equipment,
- The PLC-based Scada system is complex in terms of hardware units and connected modules.
Now we come to the part that interests us. What has been said so far was to understand Scada systems with its general logic. As everyone knows, the common point of all technologies is cyber security. Every company, every institution from every sector needs cyber security. The reason for this is that technology takes place at every stage of our lives and the common point of all technologies is cyber security. No matter what system or software you use, the costs in a cyber attack will be very high if you do not take security measures. Since this situation will cause both financial and prestige loss, it is beneficial for all companies and institutions to prioritize cyber security.
Because Scada systems monitor critical infrastructures, it is important that they are protected against cyber attacks. Scada systems are designed without critical functions such as security and protection against cyber threats. For this reason, Scada systems are defined as systems with vulnerabilities.
As an example of these vulnerabilities; The fact that the PLC component is directly connected to the sensors providing data in the field and the hard-coded default passwords to the ethernet cards are used without changing.
When we look at the components and attack surfaces that need to be secured in Scada systems;
- Programmable Logical Controller (PLC),
- Internet, Enterprise Network and Peripheral Components,
- Network Architecture,
- Network Operating Systems,
- Computer Security,
- Control System Performing Data Collection and Process Control Operations,
- Security Rules and Procedures (For example, we can say business continuity and disaster recovery)
At these points, keeping the security at a high level is important in terms of minimizing the damage in a possible cyber attack. So what are the general weaknesses of Scada systems?
- Smart grid systems may contain security vulnerabilities of the common and licensed technologies they use,
- Information technology communication systems pose a security risk if precautions are not taken,
- Communication networks connecting smart grid devices and systems provide more access points to Scada systems.
At this point, what are the security measures that can be applied in Scada systems?
- File integrity,
- Memory protection,
- Dynamic whitelisting (preventing unauthorized program and code execution),
- Read protection (this operation is authorized only for special files, directories, partitions.),
- Write protection (Hard disk writes are only allowed for services that handle the operating system, application configuration, and log files.
Let’s end our topic by talking about the defense methods that should be applied in general for Scada systems. It will be easier to understand them by listing them as items.
- To determine security policies specific to Scada systems,
- Implementing a layered network topology,
- Implementation of DMZ network architecture to prevent direct traffic between the institution and Scada systems,
- Checking whether the critical components are in the redundant and redundant network,
- Restricting physical access to Scada networks and devices,
- Managing security processes such as preventing malware infection, detecting it early, preventing its spread and reducing their damage,
- Using secure network protocols and services,
- Provide monitoring and control for critical Scada areas.
You can contact the ICSDI team to get support in the field of cyber security and to get information about our cyber security software and services.